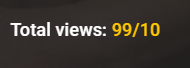
This guide will show you how to get "unlimited" premium days for your keep2share account in just a few seconds.
It's using the xfantazy method, where you get one day for each 10 views. Some people tried automating this with Selenium, which was way too overkill.
Just use the API.
There's an endpoint called
This will essentially count one view for your account. Do this with a list of proxies and you should be able to farm some views and get some premium days.
Let's write a bash script.
Before running this, you have to create a file in the same directory called proxies.txt, where you'll put all your proxies in, using the default format.
You probably want to replace <url> with the previously named website, which I can't include in the script, since it's a blacklisted word/host.
And also replace YourUserId with your account id. You can find this at the end of your referral url you've copied by clicking on "Share & Get Free Premium!".
Feel free to change the contentId, for example when the script stops working suddenly. You can also get this from said referral url.
Run this script and you'll get approximately one view for each proxy. You can reuse the same proxies later.
If you're on Windows and wondering how to run this, simply download , which will install an terminal emulator that allows you to run bash scripts. Then you can right click on the folder where your script is located in and click "Git Bash here".
Assuming you've named your file k2s.sh, run
Have fun.
It's using the xfantazy method, where you get one day for each 10 views. Some people tried automating this with Selenium, which was way too overkill.
Just use the API.
There's an endpoint called
/events/user/videoViewed, which is requested after you started watching the video for some seconds.This will essentially count one view for your account. Do this with a list of proxies and you should be able to farm some views and get some premium days.
Let's write a bash script.
Before running this, you have to create a file in the same directory called proxies.txt, where you'll put all your proxies in, using the default format.
You probably want to replace <url> with the previously named website, which I can't include in the script, since it's a blacklisted word/host.
And also replace YourUserId with your account id. You can find this at the end of your referral url you've copied by clicking on "Share & Get Free Premium!".
Feel free to change the contentId, for example when the script stops working suddenly. You can also get this from said referral url.
Run this script and you'll get approximately one view for each proxy. You can reuse the same proxies later.
If you're on Windows and wondering how to run this, simply download , which will install an terminal emulator that allows you to run bash scripts. Then you can right click on the folder where your script is located in and click "Git Bash here".
Assuming you've named your file k2s.sh, run
chmod +x k2s.sh and then ./k2s.sh.Have fun.
Last edited: